Collection is not Detection - Optimising Your SOC with Microsoft Sentinel Basic Recommendations
Optimising Your SOC with Microsoft Sentinel Basic Recommendations
Optimising your Security Operations Centre (SOC) is crucial to staying ahead of cyber threats. Microsoft Sentinel now offers actionable SOC optimisation recommendations designed to help organisations improve security posture, reduce unnecessary data ingestion costs, and align with best practices. This blog explores three core recommendation types, data value optimisation, threat-based optimisation, and similar organisations comparisons, providing practical steps to use these features yourself!
Disclaimer
This feature is a new and evolving capability. While it offers significant potential surface benefits, it is essential to seek expert advice to ensure proper implementation and alignment with your organization's unique requirements.
Additionally, it’s important to remember that all aspects of your Sentinel Instances should be regularly reviewed, maintained, and updated as part of standard best practices.
Why SOC Optimisation Matters
COST! SOC teams often face challenges balancing comprehensive threat detection with operational efficiency. The increasing volume of data ingested from various sources can lead to skyrocketing costs and wasted resources if not carefully managed. Microsoft Sentinel starts to address these pain points by providing first step specific recommendations that streamline data usage, identify coverage gaps, and leverage insights from similar organisations.
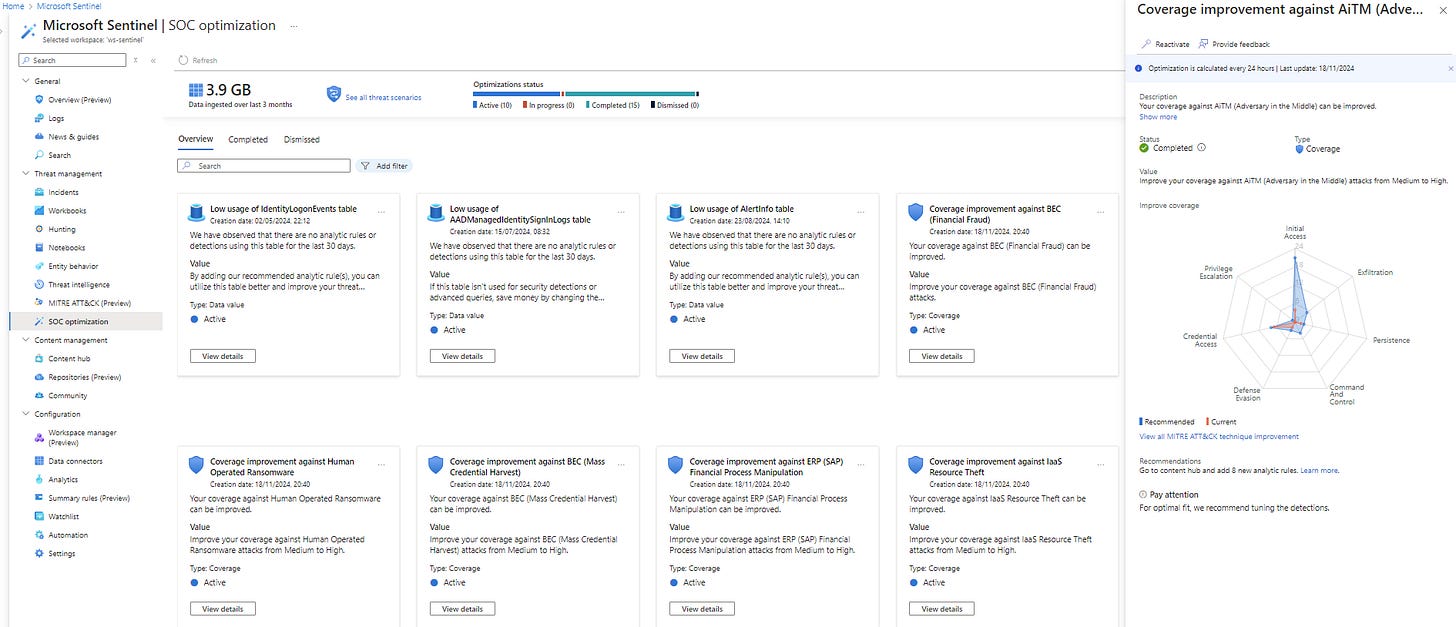
1. Data Value Optimisation Recommendations
Data value optimisation focuses on the cost-security balance by highlighting underutilised or unnecessary data ingestion. Sentinel identifies billable tables from the past 30 days and categorises their value to your security operations.
Key Observations and Actions:
Unused Tables:
Observation: A table hasn’t been used in analytics, detections, or hunting in the last 30 days.
Action: Consider turning on relevant analytics rule templates, archiving the table, or stopping ingestion entirely.
*If your data is being used by an external service or MSP / MSSP its key to ensure its not being used in another way.
Partially Used Tables:
Observation: A table is only used by Azure Monitor or similar tools.
Action: Move the table to a non-security Log Analytics workspace or enable relevant analytics templates.
Rule of thumb. The log is not security related ? = Don’t ingest it.
Pro Tip: Always ensure compliance requirements are met before modifying ingestion plans. Some tables may hold regulatory significance even if they lack immediate security value.
2. Threat-Based Optimisation Recommendations
Threat-based optimisation uses a proactive approach to close gaps in threat detection by aligning your SOC’s capabilities with industry-standard threats and attack scenarios.
Key Observations and Actions:
Missing Detections for Existing Data Sources:
Action: Turn on analytics rule templates for identified threats. Tailor the rules to your environment for maximum effectiveness.
Missing Data Sources for Existing Detections:
Action: Connect relevant data sources that enhance coverage against known threats.
No Data Sources or Detections:
Action: Deploy new detections and connect data sources, or install comprehensive solutions to address gaps.
Pro Tip: Regularly review and update detection rules to ensure they reflect evolving threat landscapes and organisational needs.
3. Similar Organisations Recommendations *
Microsoft Sentinel leverages advanced machine learning to compare your organisation’s SOC setup with others of similar size, industry, or operational trends. This unique feature provides recommendations tailored to your environment, ensuring relevance and actionable insights.
Key Observations and Actions:
Missing Log Sources:
Action: Ingest suggested data sources based on trends observed in similar organisations. Or risk accept the fact you chose not to for X reason.
Considerations:
Recommendations are only available if sufficient similarities are identified.
Early-stage SOCs benefit most, as mature SOCs tend to have fewer significant gaps.
Pro Tip: Use these recommendations to fast-track SOC maturity and benchmark against industry peers without exposing sensitive data.
Cant find this one ?
** Not all workspaces get similar organizations recommendations. A workspace receives these recommendations only if our machine learning model identifies significant similarities with other organizations and discovers tables that they have but you don't. SOCs in their early or onboarding stages are generally more likely to receive these recommendations than SOCs with a higher level of maturity.
Key Takeaways
SOC optimisation with Microsoft Sentinel empowers organisations to:
Start to reduce costs by identifying underutilised data and aligning ingestion with security value.
Close coverage gaps by implementing relevant threat-based analytics and data sources.
Learn from industry peers using machine learning-powered insights.
By implementing these recommendations, organisations can elevate their SOC efficiency, improve threat response times, and ensure their investments in security are cost-effective.
Next Steps
Take advantage of Microsoft Sentinel’s optimisation capabilities:
Evaluate your current setup: Review your data ingestion and analytics rules.
Implement recommendations: Use Sentinel’s insights to make informed decisions on resource allocation and security improvements.
Continuously optimise: Regularly revisit your SOC configuration to adapt to evolving threats and organisational growth.
For more detailed guidance, visit the Microsoft Sentinel documentation.
With a strategic approach to SOC optimisation, your organisation can stay secure, agile, and resilient in the face of growing cyber threats.
#MicrosoftSecurity
#MicrosoftLearn
#CyberSecurity
#MicrosoftSecurityCopilot
#Microsoft
#MSPartnerUK
#msftadvocate