KQL Simple Mode - Unlocking the Power of Log Analytics to all!
A Guide to Simple Mode and KQL Mode within Microsoft Log Analytics (LAWS)
In a recent announcement, Microsoft has significantly simplified the process of getting started with Log Analytics Workspace (LAWS) and Kusto Query Language (KQL), making it more accessible than ever!
Why is this so important?
Microsoft Sentinel and other Microsoft security products are built on top of Log Analytics, leveraging its robust data collection and analysis capabilities. This foundational integration means that all data ingested by Sentinel is stored in a defined Log Analytics workspace, providing a centralized and scalable repository for security data. The use of Log Analytics ensures that data is stored in a structured and accessible format, enabling seamless querying and analysis through both Simple and KQL modes.
Log Analytics or LAWS for short has taken a significant leap forward with the introduction of two distinct modes designed to cater to both novice and advanced users. These new modes make exploring and analyzing log data more intuitive and powerful than ever before.
Simple Mode: Effortless Data Exploration
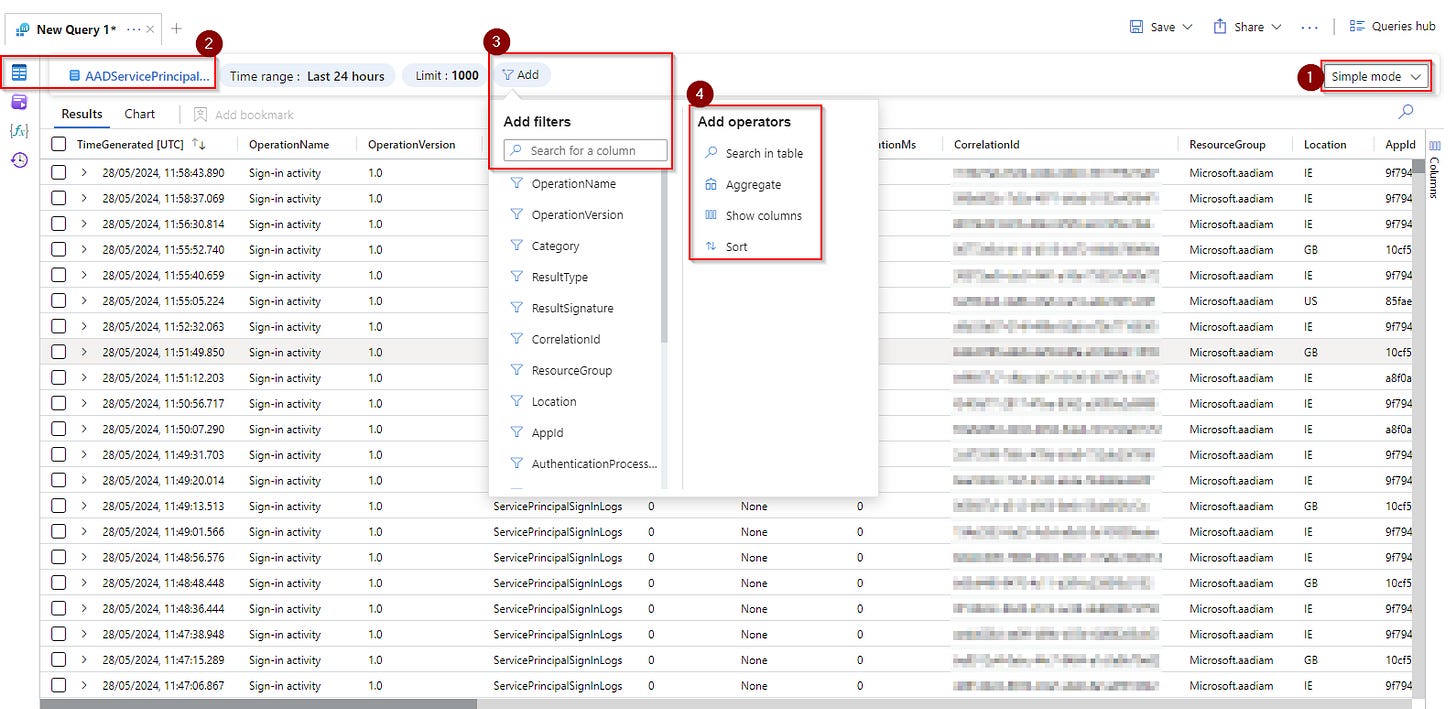
For users who need quick insights without diving deep into complex query languages, Simple mode is a game-changer. This mode offers the most commonly used Log functionality in a user-friendly, spreadsheet-like interface. With Simple mode, you can:
Filter: Narrow down your data to focus on what's important.
Sort: Organize your data for better readability.
Aggregate: Summarize data to uncover trends and insights.
Simple mode empowers you to get to the insights you need 80% of the time with just a few clicks, making it perfect for users who prioritize efficiency and ease of use.
KQL Mode: Advanced Data Analysis
For those who need more powerful tools to extract deeper insights, KQL mode offers the full capabilities of the Kusto Query Language (KQL). This mode is tailored for advanced users who are comfortable with writing complex queries to analyze their data. The Log Analytics query editor provides a robust environment for crafting and executing detailed queries that can reveal intricate patterns and correlations within your logs.
Get started in Simple mode
When you select a table or a predefined query or function in Simple mode, Log Analytics automatically retrieves the relevant data for you to explore and analyze.
This lets you retrieve logs with one click whether you open Log Analytics in resource or workspace context.
To get started, you can:
Switch to the new LAWS experience -
Click Select a table and select a table from the Tables tab to view table data.
By default, Simple mode lists the latest 1,000 entries in the table from the last 24 hours.
Remember the maximum number of results that you can retrieve in the Log Analytics portal experience, in both Simple mode and KQL mode, is 30,000.
For more info check out the official documentation or start learning KQL today!
Check out
and his posts, Must Learn KQL Part 1: Tools and ResourcesHappy Querying!
#MicrosoftSecurity
#MicrosoftLearn
#CyberSecurity
#MicrosoftSecurityCopilot
#Microsoft
#MSPartnerUK
#msftadvocate