Defender Secure Score - Intune Endpoint Manager / Windows / Accounts / Disable the local storage of passwords and credentials
How to remediate "Disable the local storage of passwords and credentials" secure score recommendation via Microsoft Intune / Microsoft endpoint manager.
Trying to make it to 100% within Microsoft Secure Score? Here is a common remediation item “Disable the local storage of passwords and credentials” under the “Accounts” category that Microsoft dose not give you an OOTB cloud only solution / recommendation to.
Understanding the "DisableDomainCreds" Registry Value
The "DisableDomainCreds" registry value, located within the HKLM\SYSTEM\CurrentControlSet\Control\Lsa key, plays a vital role in bolstering system security. When set to a REG_DWORD value of 1, it ensures that domain credentials are disabled, significantly reducing the risk of unauthorized access and potential security breaches.
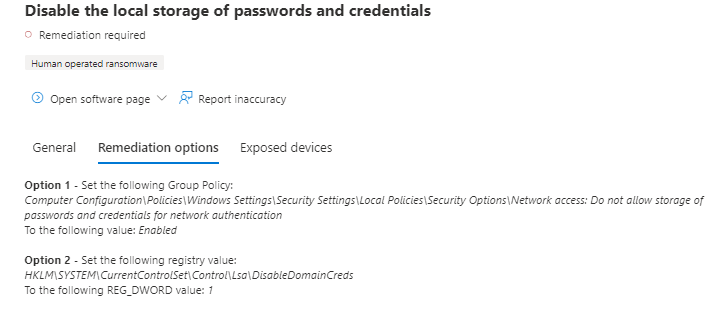
Microsoft’s Remediation advice
Option 1
Set the following Group Policy:
Computer Configuration\Policies\Windows Settings\Security Settings\Local Policies\Security Options\Network access: Do not allow storage of passwords and credentials for network authentication
To the following value: Enabled
Option 2
Set the following registry value:
HKLM\SYSTEM\CurrentControlSet\Control\Lsa\DisableDomainCreds
To the following REG_DWORD value: 1
Microsofts The problem with HKLM\SYSTEM\CurrentControlSet\Control\Lsa\DisableDomainCreds
But how can we do this with Intune?
This advise dose not include a config profile or template setting. The item dose not actually exist in the Settings catalog.
Even searching keywords such as “LSA” Domain” Network”
Remediations options (Intune Native)
Package a Win 32 App with Script - Old method.
Use a proactive remediation. - New most efficient way. - The below will overview this.
Step 1: Detecting the Current Registry Value
Before making any changes, it is crucial to determine the current state of the "DisableDomainCreds" registry value. To achieve this, we will use a PowerShell detection script that can be executed through Microsoft Intune. The script checks if the current value matches the desired value (1). If it does, the setting is already configured correctly. Otherwise, the script will indicate that the setting needs remediation.
Step 2: Remediation with Microsoft Intune
With the detection complete, it's time to proceed with the remediation process using Microsoft Intune. The remediation script, also written in PowerShell, modifies the "DisableDomainCreds" registry value to the desired value (1). By leveraging the capabilities of Intune, you can efficiently deploy and enforce these changes across multiple devices in your organization.
Here's an example of a PowerShell script that includes both the detection and remediation scripts to set the "DisableDomainCreds" registry value using Microsoft Intune:
Detection Script:
# Define the path to the registry key
$Path = "HKLM:\SYSTEM\CurrentControlSet\Control\Lsa"
# Define the name of the registry value to check = VALUENAME
$Name = "DisableDomainCreds"
# Define the expected value of the registry value = VALUE DATA
$Value = "1"
# Retrieve the value of the registry value
$Registry = Get-ItemProperty -Path $Path -Name $Name -ErrorAction SilentlyContinue | Select-Object -ExpandProperty $Name
# If the registry value matches the expected value, output "Compliant"
If ($Registry -eq $Value){
Write-Output "Compliant"
Exit 0
}
# If the registry value does not match the expected value, output "Not Compliant"
Else {
Write-Warning "Not Compliant"
Exit 1
}In the detection script, we retrieve the current value of the "DisableDomainCreds" registry entry. If the value matches the desired value, it means the setting is already configured correctly, and the script exits with a success code (0). Otherwise, the script exits with a failure code (1), indicating that the setting needs to be remediated.
Remediation Script:
# Define the path to the registry key
$Path = "HKLM:\SYSTEM\CurrentControlSet\Control\Lsa"
# Define the name of the registry value to check
$Name = "DisableDomainCreds"
# Define the expected value of the registry value
$Value = "1"
# Retrieve the value of the registry value
$Registry = Get-ItemProperty -Path $Path -Name $Name -ErrorAction SilentlyContinue | Select-Object -ExpandProperty $Name
# If the registry value matches the expected value, output "Compliant"
If ($Registry -eq $Value){
Write-Output "Compliant"
#Exit 0
}
# If the registry value does not match the expected value, remediate and output "Fixed"
Else {
Write-Warning "Not Compliant. Attempting remediation..."
# Set the registry value to the expected value
Set-ItemProperty -Path $Path -Name $Name -Value $Value -Force
# Verify remediation
$RemediatedRegistry = Get-ItemProperty -Path $Path -Name $Name -ErrorAction SilentlyContinue | Select-Object -ExpandProperty $Name
if ($RemediatedRegistry -eq $Value) {
Write-Output "Fixed"
Exit 0
} else {
Write-Warning "Remediation failed"
Exit 1
}
}The remediation script sets the "DisableDomainCreds" registry value to the desired value using the `Set-ItemProperty` cmdlet. If the operation is successful, the script exits with a success code (0). Otherwise, it exits with a failure code (1), indicating that the configuration failed.
Intune Proactive Remediations Settings
Detection script
Yes
Remediation script
Yes
Run this script using the logged-on credentials
No
Enforce script signature check
No
Run script in 64-bit PowerShell
Yes
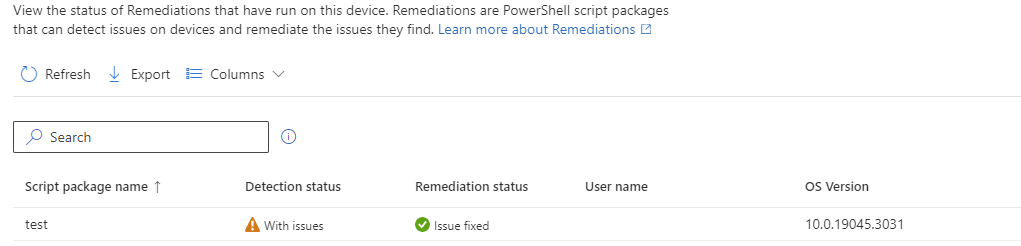
Results
Detection Script Status
The expected result on the detection scrip if the value dose not already exist is “With Issues”. This is by design - See screenshot of GitHub question below. This is for another topic but applies to Remediation Scrips in general.
Device Remediated
Warning
Please note that running registry modifications can have significant system impact, so it's essential to thoroughly test and validate the script in a controlled environment before deploying it widely. Additionally, make sure you have the necessary administrative privileges to modify the registry on target devices.
Benefits of Leveraging Microsoft Intune for Registry Configuration
Microsoft Intune provides several advantages when it comes to managing registry settings and configurations. Some of the key benefits include:
Centralized Management: Intune offers a centralized platform to configure, monitor, and enforce registry settings across a fleet of devices, reducing the administrative burden and ensuring consistency.
Scalability: Whether you have ten devices or thousands, Intune scales effortlessly, enabling you to manage security settings efficiently across your entire organization.
Automation and Compliance: Intune's automation capabilities allow you to automate the deployment of registry changes and ensure compliance with security policies, mitigating potential risks.
Real-time Monitoring and Reporting: Intune provides real-time monitoring and reporting capabilities, allowing you to track the status of registry configurations, detect anomalies, and quickly address any issues that may arise.
Conclusion
Configuring registry settings is a critical aspect of maintaining a secure IT environment. By utilizing the power of Microsoft Intune, you can streamline and automate the process, reducing the likelihood of unauthorized access and potential security breaches. In this blog post, we explored the importance of the "DisableDomainCreds" registry value and provided a step-by-step guide for detecting and remediating this setting using Intune. By following these guidelines, you can effectively fortify your systems against unauthorized domain credential usage, enhancing your overall security posture. Leverage the capabilities of Microsoft Intune today and take proactive steps towards a more secure IT infrastructure.
Microsoft Community Q&A Question
Items to consider as prerequisites / context reads.
What is Microsoft Defender Secure Score? - LINK
What is Microsoft Endpoint Manager Remediations? - LINK
What method have you used?
Let us know in the comments any “Other” suggestions!
Thanks for reading. Any suggestions on future posts - Contact me!





Diogo, Greetings !
Thank you for my First EVER blog post comment. Really appreciate the feedback and I’m glad it’s helped!
This "Set 'Minimum password length' to '14 or more characters'" will be in a blog post as soon as I get time!
If you found this Blog via the Microsoft Community page. It would be greatly appreciated to upvote the answer to help other also !
Have a great day!
Very cool, thank you. This helped big time!